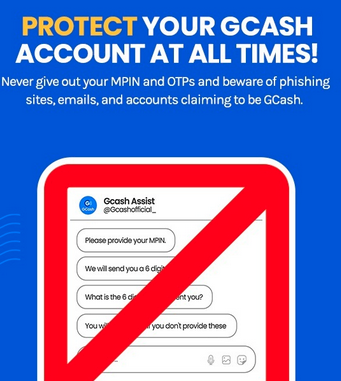
After a couple of weeks of investigation by the National Privacy Commission (NPC), it was independently concluded that the widespread fraudulent transactions with GCash last May 8 was due to phishing exploits on unsuspecting GCash users.
Overnight, more than 300 people reported that their GCash accounts made unauthorized transfers to two bank accounts from East West and AUB.
The following day, GCash confirmed that indeed there were repeated/unusual transactions in their system that triggered internal systems and immediately coordinated with the affected bank to freeze the accounts.
GCash has likewise assured the public that there was no hacking involved and that there was “no fund loss” on the part of the customers.
That same day, we posited a theory that all these incidents were just a carefully planned and well-coordinated attempt to simultaneously execute the transfers from phished accounts in order to make it look like a hacking incident.
The NPC investigation will finally close any and all suspicions about the GCash incident. All affected customers has also been refunded of their missing funds.
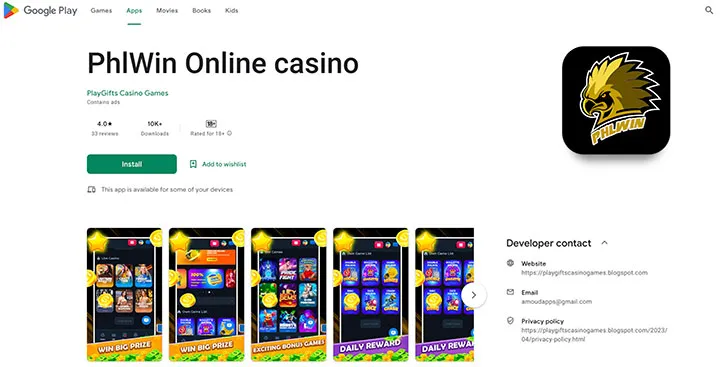
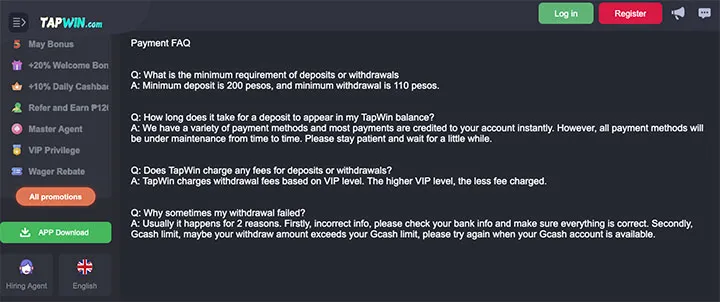
GCash has also finally revealed, thru the NPC report, that two gambling sites were primarily involved in the phishing expedition — Philwin and tapwin1.com.
According to the Google Play Store, Philwin is the “#9 casino apps” in the store. It has over 10,000 downloads and 33 reviews. The first app review was posted May 3 and the latest in May 23, all averaging 4 stars.
A cursory check of the developer revealed very little information such as a BlogSpot website and no developer name. Sketchy.
TapWin1.com, on the other hand, looks more decent and well made with an active social media presence. A quick check at their FAQ also showed they’re actively using GCash to top up and withdraw money from users.
The next move here is for the NPC (or the DOJ) to file a case agains these sites under the Anti-Cybercrime Law and have these sites/apps shut down permanently.
Full story here: https://tinylinkurl.com/yaLsu






Comments
Authentication required
You must log in to post a comment.
Log in